Tech Terms
DevSecOps (dev·sec·ops)—short for development, security, and operations—automates the integration of security at every phase of the software development lifecycle, from initial design through integration, testing, deployment, and software delivery.
Releasing the Hounds on Ransomware
What’s New: Governments around the world are fixing their sights on the ransomware scourge — and things are getting real.
Why This Matters: The number of annual ransomware attacks doubled in just the first half of 2021 and attackers are growing more aggressive, more reckless, and more sophisticated.
Key Points:
In the first six months of 2021, 23 ransomware groups attacked more than 1,000 organizations, in 18 different industries, across 66 countries.
Earlier this month, the Biden Administration hosted a multi-national virtual summit on ransomware, resulting in this joint statement.
Since then, Washington, Canberra, and London have announced specific plans to confront ransomware attacks, including the U.S. Department of State creating a new a Bureau of Cyberspace and Digital Policy to be led by a Senate-confirmed ambassador-at-large and a new, separate Special Envoy for Critical and Emerging Technology.
But governments are doing more than just creating new org charts. In fact, a multi-nation cyber operation recently bricked1 the infrastructure of the REvil ransomware group — the one responsible for attacking the U.S.’ Colonial Pipeline this summer — setting off a hissy fit among the black hats2.
What I’m Thinking: I’ve said a lot about ransomware. If you don’t remember, you can catch up here, here, and here. Bottom Line: the U.S. intelligence/military enterprises should specifically be tasked to identify, deter, disrupt, and dismantle foreign ransomware attackers and their networks. These attacks should be treated as cyberterrorism and nation states who enable or harbor these attackers should be engaged accordingly. The reality is that we’re not going to be able to deny this capability to people who want to cause havoc, and so we must do what is necessary to make these attacks so costly, so painful for the bad guys, that they decide the rewards aren’t worth the risk. If the bad guys want to fight back — game on.
Counterintelligence’s Top Tech Targets
What’s New: Michael Orlando, acting director of the National Counterintelligence and Security Center (NCSC), says he’s narrowing his focus to safeguarding five key technologies, according to the Wall Street Journal.
Why This Matters: The NCSC says AI, quantum computing, bioscience, semiconductors, and autonomous systems will be key to ensuring America remains the world’s leading superpower.
Key Points:
This adjustment is a continuation, not a departure, from efforts begun in the Trump administration to engage with universities and industry, to stop the theft of critical IP and research by foreign actors — most notably the Chinese government.
The agency also named Edward You — a FBI agent with expertise in biological threats — to a newly-created position focusing on emerging and disruptive technologies.
Orlando explained these actions by arguing that it is no longer practical for the Center to look at the broader field of technologies and that certain threats — like Chinese managed telecommunications equipment — are already well known.
What I’m Thinking:
These five technologies certainly deserve our attention. Each of these technologies have broad and disruptive civilian and military applications. We need to protect them and lead in their development and deployment.
But this narrowing reflects a lack of resources, not concerns. In saying that “it is no longer practical,” the NCSC acting director is tacitly admitting that his agency cannot keep up with the demands of the mission. That’s not surprising or good.
This is a whole of society challenge. One agency cannot be expected to unilaterally prevent Chinese technological espionage, let alone all technological espionage. Instead, we need two things to happen: First, the U.S. government needs to establish persistent, detailed, and relevant information sharing with the private sector regarding bad guy intentions, capabilities, and activities. Second, private companies have to accept that they are now a key battleground for geopolitical influence and, as such, must make decisions about where and how they operate accordingly. Doing business in and with China is not only about short-term bottom lines, but also about creating economic and military capacity and leverage for the U.S.’ chief rival. Until now, the Chinese government has been the one making life difficult for U.S. companies; but, we are quickly approaching days when it will also be the American government demanding changes. Businesses can ignore this (for now), but they will not be able to avoid it.
DoD’s Hidden AI Talent
What’s New: The rockstars at the Center for Security and Emerging Technology (CSET) say the Pentagon’s AI workforce is better than popularly understood, but needs to be managed more effectively.
Why This Matters: “…We argue that DoD already has a hidden cadre of AI and related experts. We further argue that this hidden cadre could go a long way in meeting stated AI objectives …”
Key Points:
For its analysis, CSET interviewed 31 experts from the Office of the Secretary of Defense and from each of the services.
They then analyzed personnel data from the Office of Personnel Management (OPM) and previous CSET research.
The authors discovered that the U.S. national security community is one of the top employers of AI talent, but that DoD’s portion of this workforce “remains hidden.”
This talent pool is hidden because the military does not have a consistent methodology for defining AI priorities or those working on these priorities. This challenge is then broken down into three categories: people, processes, and technology.
In response, CSET has 15 recommendations that cover technical and nontechnical talent, apply to each of the services, are broken down by challenge, and are intentionally actionable on short- and medium-term timelines.
“Our analysis found that each service has its own office or organization that oversees what it loosely considers ‘AI talent,’ either formally or informally. Across these entities, AI talent is most commonly identified through informal networks and personal connections, with interviewees across all services highlighted heavy reliance on such networks to find suitable talent. While other methods of identification exist, they are imperfect, such as equating an existing career field or educational credential with AI expertise. Interviewees across the enterprise stressed the lack of an effective, systematic means to identify AI talent quickly and accurately.”
What I’m Thinking:
I’m encouraged and I don’t get to say that very often. The normal narrative is that the military cannot compete with industry for top-tier AI talent. And, to a degree, that is true. But that doesn’t mean that DoD has no AI talent and this analysis suggests that the talent it has is actually really good!
Now we must leverage this talent. CSET suggests that relatively modest improvements in people management, processes, and technology could go a long way in meeting the Pentagon’s AI requirements. Most fundamentally, this report calls for agility in talent management and reforms to the Joint Artificial Intelligence Center so that it more effectively operates as the central hub and coordinator of DoD AI activities.
I hope DoD listens. You can read more of the report’s findings and recommendations by clicking on the attachment below.
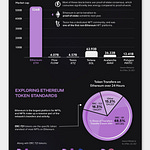
Let’s Get Visual
Nerd Humor

Quick Clicks
I joined the ladies over at Pantsuit Politics to talk about cybersecurity (listen)
North Korea continues to fund its nuclear program by hacking banks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!
To “brick” is to render a piece of hardware unusable.
A “black hat” hacker is one who engages in illegal hacking, often for financial gain or destructive purposes.