Heads Up
Bill Drexel and I have a new article arguing that the United States and Taiwan need unprecedented cooperation in order to secure the island from Chinese invasion and cyber attacks.
“In the domain of Sino-American tech rivalry, Taiwan is unique in two aspects: First, the Taiwan Semiconductor Manufacturing Corporation (TSMC) remains the world’s tightest bottleneck in the global high-tech ecosystem, with exclusive capabilities to construct the most valuable, sophisticated computer chips in existence. Second, military conflagration in Taiwan would represent a hitherto-unknown level of cyber-intensive military conflict, the seeds of which likely have already been planted. Both of these realities demand unprecedented cooperation between the United States and Taiwan—cooperation that requires significant trust and openness in Taipei and significant counter-espionage and national security assistance from Washington.”
Tech Terms
Secure Socket Layering (SSL) — SSL is a protocol that allows Internet users to send encrypted messages across the Internet. It is generally used when transmitting confidential information (e.g. personal data or credit card details). A web address that begins with "https" indicates that an SSL connection is in use.
Tech Policy as Coercive Diplomacy
What’s New: The United States is considering sanctions that would deny Russia access to key technologies as the two nations face off over Ukraine.
Why This Matters: As technology grows in economic, social, military, and political importance, so does its potential as a means of leverage in global affairs.
Key Points:
The Biden administration is putting together a suite of actions, according to the New York Times, that would “target some of Mr. Putin’s favored industries — particularly aerospace and arms, which are major producers of revenue for the Russian government.”
“The focus would be on Russian-built fighter aircraft, antiaircraft systems, antisatellite systems, space systems and emerging technologies where Russia is hoping to make gains, like artificial intelligence and quantum computing,” says the New York Times story.
The proposed sanctions would ban Russia from purchasing semiconductors that rely on American design, as well as machines that use these chips — everything from mobile phones, to personal computers, to dishwashers and refrigerators.
What I’m Thinking:
This is a modernized version of a proven foreign policy tool. Coercive diplomacy is a long-practiced and formally-studied form of statecraft. The general idea, as explained by Alexander George in The General Theory of Coercive Diplomacy, is to “back one's demand to an adversary with a threat of punishment for noncompliance that he will consider credible and potent enough to persuade him to comply with the demand."1
There are three general strategies of coercive diplomacy. First, you can issue an ultimatum — drawing a “redline” and giving a drop-dead date for compliance. Second, you can “try-and-see.” In this case, an ultimatum is issued but no deadline is given and the threatening party observes the behavior of its target and adjusts accordingly. Finally, third, you can “turn the screw,” where a target is told what behavior is expected and pressure or punishment are incrementally increased. The first strategy is the most aggressive while the second and third strategies allow for more agility. Right now, the United States appears to be employing the second strategy but may shift to the third approach after a Russian invasion.
Tech sanctions are powerful and play to U.S. strengths, but they are no silver bullet. Even though the United States does not manufacture most of the world’s technology, it does play a decisive role in their design and in consumer demand. Leveraging this point of power has proven effective in the case of China and Huawei, for example. By working with foreign semiconductor manufacturers to deny access to advanced chipsets, the United States has crippled the telecommunications company’s ability to innovate or even meet current requirements — causing profits to fall nearly 30% last year. Even so, Russia’s consumers are not nearly as demanding for technological goods as are China’s, and if punishing sanctions are imposed, it is possible Russians would primarily blame the United States, and not the Kremlin, for the disruption. Beyond this, however, cutting off Moscow from key tech could dramatically constrain the nation’s military industry which is a key source of economic strength and is likely being considered very seriously by Putin — with Russian markets dropping 6% this week after the apparent breakdown of U.S. talks.
Crypto Mining Goes Down With Kazakhstan
What’s New: Once a crypto currency center of gravity, political unrest and other problems are killing Kazakhstan’s digital mining industry.
Why This Matters: The nation’s unstable political situation and unreliable power and other essential services are gutting its once-growing crypto mining economy — costing the nation millions and further inflaming domestic frustration.
Key Points:
Miners compete to complete “blocks” of verified transactions, which are then added to the coin’s digital ledger, called the “blockchain.” (Here’s a simple infographic if you’d like to learn more)
Mining “rigs” — groups of networked computers — either use application-specific integrated circuits (ASIC) or graphics processing units (GPU) to complete these calculations, both of which require substantial computational power and energy consumption.
After China shut down crypto mining within its borders last year, Kazakhstan became an attractive alternative because of its relative proximity, permissive legal environment, and rich energy sources. As many as 87,849 machines relocated to Kazakhstan, accounting for more than 18% of the global Bitcoin mining as of last August.
That’s all changing as fuel prices surge, Kazakhs protest, and Russian troops roam the country.
Even as Kazakhstan’s President Kassym-Jomart Tokayev has restored some semblance of order — backed by the Russian military — internet and power outages continue and crypto mining declined by more than 12% last week.
The recent protests began over fuel prices, but are also about longer-standing issues like economic weakness and income inequality — none of which are going away.
What I’m Thinking:
It’s a short hop from crypto boom to bust. Kazakhstan is an example of how a nation can realize new opportunities with new technologies but also how those same technologies can strain a nation’s underlying capacity. It didn’t take long for crypto mining to push the country’s energy infrastructure to the brink, forcing the government to shut down a major mining farm in November. Throw in a healthy dose of political instability and you get yet another dynamic that geostrategists must now account for as they seek to understand and shape the international order.
Commerce Considering Cybersecurity Labels
What’s New: The U.S. government is considering nutrition-like labels to help consumers assess cyber risk, according to the Washington Post.
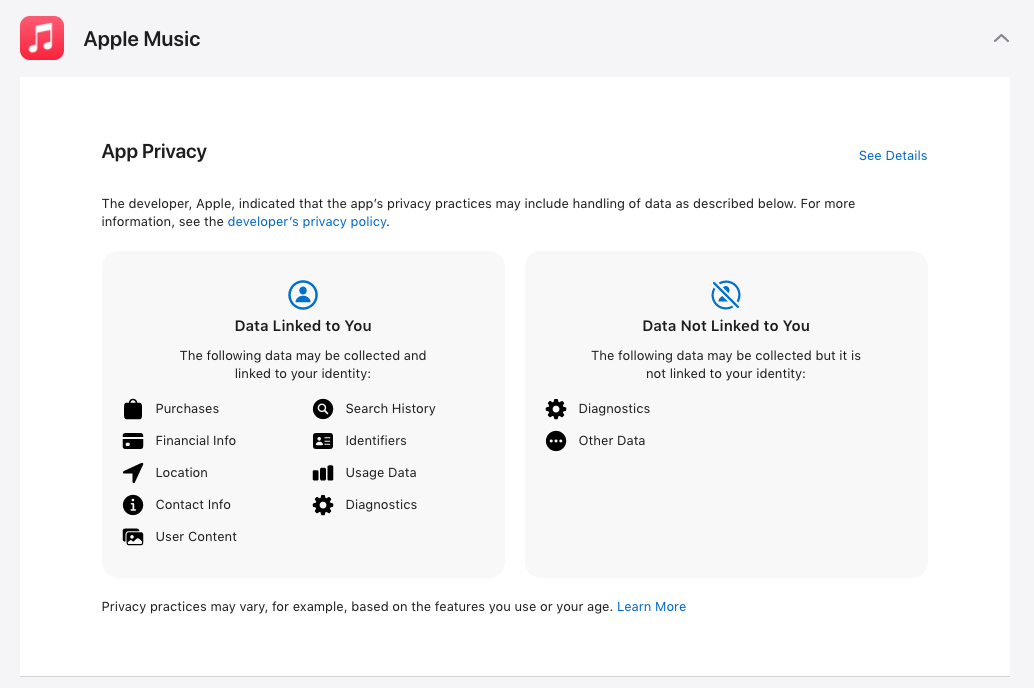
Why This Matters: Similar labeling efforts have been considered and implemented in related contexts — for example, Apple uses simple labels to help app store customers understand what data apps collect.
Key Points:
The National Institute of Standards and Technology (NIST) is running lead on a set of standards for the labels — intended to help consumers know which of their internet-connected devices is most vulnerable for hacking.
Ideally, the standards will allow industry to voluntarily adopt a verification and labeling program that tells users how good (or bad) a device or service is when it comes to basic cybersecurity practices like patching and information security.
The government hopes this will eventually work the same way energy efficiency labels work on U.S. appliances.
“Making security relatable to someone's daily life and how it can impact them is really critical for the success of this,” Julie Haney, an NIST computer scientist who’s working on the project.
What I’m Thinking:
Growing consumer awareness is a good thing. As explained, the government is not rolling out new regulations. Instead, it’s issuing a set of standards that companies can voluntarily meet and reference so that customers can make more informed choices. In light of the fact that more than 64 billion internet-connected devices are expected to be online by 2025, this seems like a generally easy and non-intrusive effort at improving the nation’s cybersecurity.
Let’s Get Visual
Nerd Humor
Quick Clicks
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!
Alexander George, "The General Theory and Logic of Coercive Diplomacy," part in Forceful Persuasion: Coercive Diplomacy as an Alternative to War, (Washington, D.C.: United States Institute of Peace Press, 1991), pp. 4