Tech Terms
API (Application Programming Interface) — A computer programming term meaning a series of rules that allow two programs to “talk” to one another. APIs allow an application to extract information from a service and use that information in their own application, or sometimes for data analysis.
U.S. & India Jointly Developing Air-Launched UAVs
What’s New: Washington and New Delhi will partner to create air-launched unmanned aerial vehicles (ALUAVs), according to The Times of India.
Why This Matters: The agreement is hoped to enable the future production of AI-enabled drone swarms that could hunt in packs and overwhelm enemy defenses.
Key Points:
The agreement calls for $22 million ($11 million from each partner) to be spent on building an ALUAV prototype under a bilateral Defense Technology and Trade Initiative (DTTI) that was launched in 2012.
“The agreement is a significant step towards deepening defense technology collaboration between the two nations through co-development of defence equipment,” said an Indian Ministry of Defence statement.
The DTTI has seven projects, including three short-term efforts — ALUAVs, lightweight small arms technologies, and ISTAR (intelligence, surveillance, targeting, and reconnaissance) systems.
What I’m Thinking:
Collaboration is good. India is a strong ally and projects like these not only help build military interoperability, but also broader political and economic ties that will translate into even greater readiness and capacity.
ALUAVs are a bit of a novelty, but still cool. Being able to drop a swarm of smaller drones from an airplane essentially enables a more rapid deployment of the UAVs, potentially mitigating some risk of discovery or disruption. For example, if a high-altitude, stealth plane or drone could transport a “bomb” full of these ALUAVs and then quickly drop them into a battle space, this could significantly increase their loiter time and survivability.
China’s Data Security Law Has Big Implications
What’s New: On September 1, China’s new Data Security Law (DSL)1 went into effect and CSIS’ Jacqueline Lee has done a great summary of what it entails.
Why This Matters: This new law will impact all business operations in China (for Chinese and foreign companies) and some operations beyond the nation’s borders.
Key Points:
Beijing’s pressure on tech companies has been mounting and seems to have significantly increased after the DSL was announced in June — with the government upping its scrutiny of companies, pushing regulatory changes, and even banning some actors.
Critically, the DSL applies to all data processing that occurs inside of China and to all data held by Chinese companies no matter where they operate, if they are deemed to “harm the national security, the public interests, or the lawful interests of citizens or organizations.”
The DSL categorizes data into “important data,” “national core data,” and “controlled items.”
Important Data is not specifically defined, but is instead a catch-all term and has previously included geolocational information associated with vehicles, military and commercial sites, and government facilities.
National Core Data includes “all data related to ‘national security, the lifeline of the national economy, important people’s livelihood, vital public interests, and other aspects.’”
Controlled Items include information that will have export controls in order to protect “national security interests” and to comply with “international obligations.”
Finally, the DSL calls for a state-planned and regulated data trading market, that will assess risk, provide reporting, enable information sharing, and govern a data security review system.
“The DSL and updated Cybersecurity Review Measures both significantly expand the government’s ability to restrict Chinese companies’ market activities. This enhanced scrutiny is not limited to Chinese companies in foreign markets,” says the report. “In July, WeChat — in order to ‘align with relevant laws and regulations’— temporarily suspended registration for new users from mainland China. After Alibaba’s Ant Group’s record-breaking $37 billion IPO, China’s antitrust regulators promptly cancelled the offering. And most recently, securities regulators tightened scrutiny over IPO price-setting in the technology-focused STAR Market stock exchange, punishing 19 institutions, citing ‘weak internal controls’ and ‘non-compliance with stipulated procedures.’”
What I’m Thinking:
In once sense, the DSL is just the latest example of the Chinese Communist Party’s (CCP) efforts to simultaneously prevent technology companies from becoming so informationally and economically powerful that they legitimately challenge the authority of the government, while the government also tries to leverage the data of these companies for the benefit of the state.
One thing is clear and every U.S. tech company must deal with it: you cannot do business in China without total capitulation to the CCP — by law. If Beijing is willing to potentially knee-cap their own state-backed champions, Western corporations have no reason to believe they would avoid a similar fate.
The dream of doing responsible business in China, free from government coercion and in a manner that doesn’t inherently threaten the interests and property of Western companies and governments, is dead. And it is the CCP who killed it.
DoD Struggling for Information Advantage
What’s New: CNAS’s Chris Dougherty has an interesting commentary over at War on the Rocks, where he claims the Pentagon’s joint warfighting concept is proving insufficient for modern battlefields.
Why This Matters: “The Defense Department has been developing the concept for years,” says Dougherty, “and yet it still failed.”
Key Points (from the article)
Nearly three years after the 2018 National Defense Strategy identified gaining and maintaining information advantage as a critical mission, thinking among Defense Department leadership about information advantage remains muddled.
The Pentagon should accept that the post-Gulf War era of imagined U.S. information dominance is over and abandon the idea of connecting “every sensor to every shooter.”
Instead, it should design its concepts around the fact that degradation, disruption, and disorder are endemic features of warfare and focus on connecting enough sensors to enough shooters under combat conditions.
The department should build new networks and data processing technologies, but it should also recognize the critical role of humans in the emerging “techno-cognitive confrontation” with China and Russia.
Gaining information advantage requires accompanying new technologies with updated command philosophies, organizational constructs, and training paradigms that will allow U.S. forces to prevail in the chaotic conditions that will characterize great-power conflicts.
The alternative is more failure and possible military defeat.
What I’m Thinking:
Dougherty lays out a larger argument. If your eyes didn’t glaze over reading the “key points,” you should read the whole article.
For the non-doctrine nerds — the author’s primary point is that a lot of military strategy and doctrine assumes the U.S. ability to “know” and to “share.” But, Dougherty says, our lived experience and countless war games demonstrate that this is not a safe assumption and that real-world war is likely to be crowded, confused, and chaotic. We should plan for THAT world.
Bottom line: We have to survive disruption and then use it to our advantage.
“If China or Russia attacks the United States or its allies and partners, it will want to keep the conflict limited and tightly controlled. U.S. forces that can operate effectively after absorbing punches in space, cyberspace, and the electromagnetic spectrum negate the idea of a quick, limited war. American counterattacks, combined with the fog and friction of conflict, will degrade Beijing’s and Moscow’s detailed operational pictures and disrupt the ability of their leaders to maintain tight control of their armed forces.”
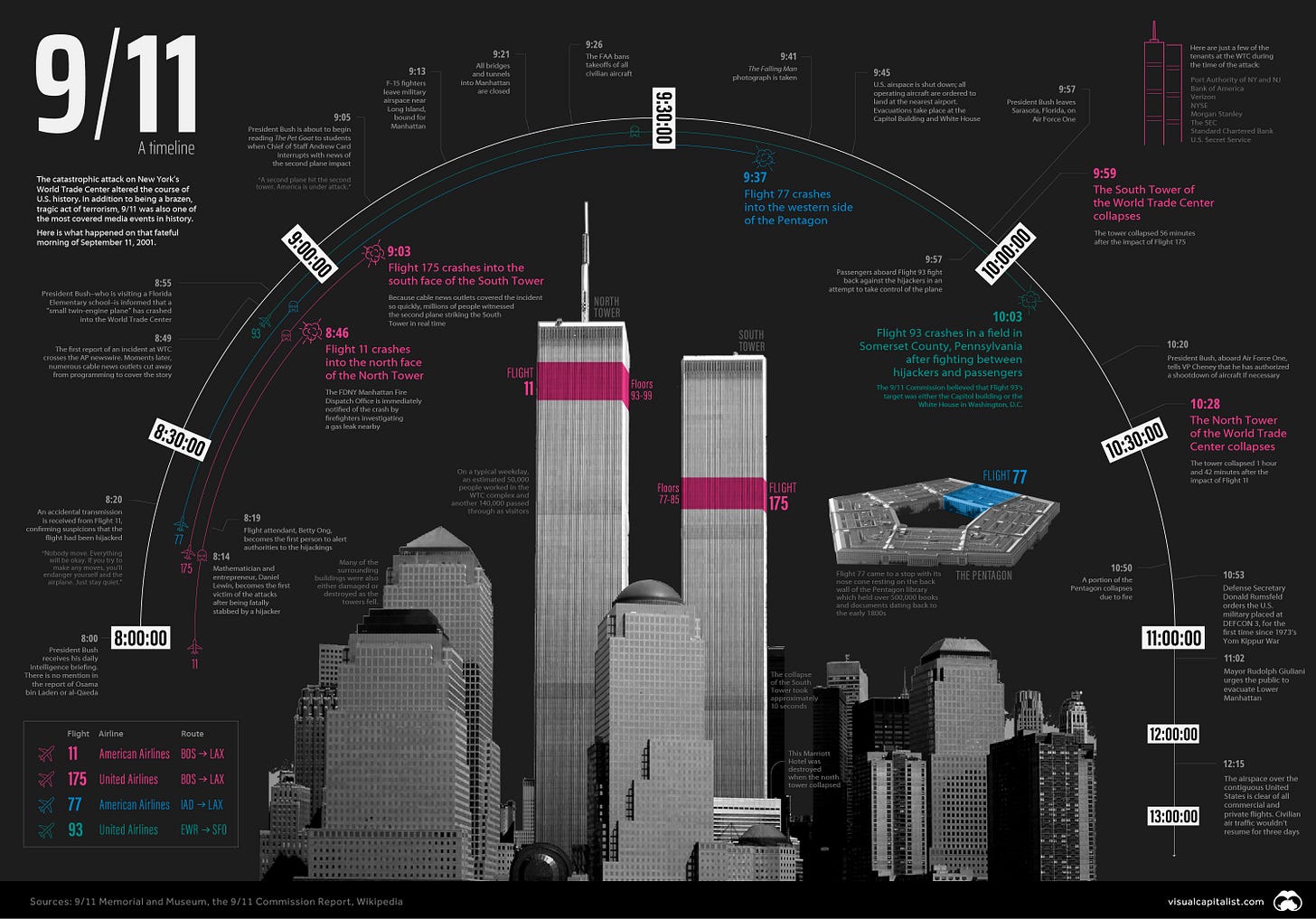
Let’s Get Visual: A Timeline of 9/11
Nerd Humor

Quick Clicks
El Salvador becomes first country to adopt crypto as national currency
McCarthy threatens tech companies who comply with January 6 inquiry
Brazil’s president bans social networks from removing some posts
That’s it for this Friday Brief. Thanks for reading, and if you think someone else would like this newsletter, please share it with your friends and followers. Have a great weekend!
DraftLast save 3:02 pm
SettingsPublish →